64.277.120.231: Why This Strange Entry Keeps Appearing in Your Server Logs
You open your access log or firewall report, and there it is again: 64.277.120.231. At first glance, it looks like a normal IPv4 address, but something feels off. You know the rules: an IPv4 address has four numbers separated by dots, and each number must stay between 0 and 255. The second part here is 277, which is impossible. That single detail tells you instantly that 64.277.120.231 cannot belong to any real device on the internet.
Yet the entry keeps appearing. Sometimes once a day, sometimes dozens of times in an hour. As a system administrator, developer, or security analyst, you need answers. This complete guide explains exactly why 64.277.120.231 and similar malformed addresses show up, where they come from, whether they pose any risk, and, most importantly, how to handle them without wasting your time.
Understanding the Problem: What Makes 64.277.120.231 Invalid
Every IPv4 address uses exactly 32 bits split into four octets. Each octet can only represent values from 0 to 255 because 255 is the largest number you can store in eight bits. When software tries to record the address 64.277.120.231, the second octet breaks that limit. Routers and operating systems immediately recognise the mistake and drop the packet. No server, no droplet, no home computer anywhere in the world can actually own this address.
Because the address is invalid from the start, real users cannot connect from it, and legitimate services cannot host anything there. The only way 64.277.120.231 ends up in your logs is when something, usually automated, writes it there by mistake or on purpose. WagerWiselyToday1,
The Most Common Reasons You See 64.277.120.231 in Logs
Bot traffic remains the number one source. Many scanning tools and low-quality crawlers generate random addresses to probe websites. Their code picks four numbers without checking the 0–255 rule, so values like 277 slip through. These bots bang on millions of websites. They hunt for open doors, old plugins, or easy passwords. When your site gets one of these knocks, it writes down the address exactly as the bot gave it, even if the address is silly and fake.
Another big reason is lazy or broken tools. Some check-up programs or test scripts use 64.277.120.231 as a pretend address while the coder is building them. Then the coder forgets to change it later. So every “are-you-alive?” check from that tool puts the same fake address in your log.
Proxy servers can also pass on junk. If a visitor hides behind a bad proxy, the proxy might send the wrong address in its note. Your server believes the note and writes 64.277.120.231 even though the real person is somewhere else. AbuseIPDB2
Last, tiny bugs in the logging code can mess things up. One wrong number or a small mix-up can turn a real address like 64.227.120.231 (a normal DigitalOcean server) into the broken 64.277.120.231. It’s just a typo made by the computer.

How to Check 64.277.120.231 Quickly and Correctly
Start with basic validation. Open a terminal and try to ping the address. The command fails instantly because no route exists. Next, run it through any online IP lookup tool. Within seconds, the tool reports “invalid format” and stops further checks.
For a deeper look, visit AbuseIPDB and search for the address. Because 64.277.120.231 is a fake address, no one can use it. So when you look it up on sites like AbuseIPDB, you see nothing. Zero bad reports. Zero complaints. Nothing at all. Most danger lists don’t even mention fake addresses because bad guys can’t attack from them.
If you want to be extra sure, check the closed real address 64.227.120.231 (just 227 instead of 277). That one belongs to DigitalOcean in New York and is almost always safe and clean.
Step-by-Step Server Log Analysis When You Spot 64.277.120.231
Open your access or firewall log and search for the exact string 64.277.120.231. Look at the timestamp, requested path, HTTP method, and user agent on the same line. Most of the time, it’s the same old story over and over: the bot keeps trying to open /wp-login.php, /admin, or pages with silly, random names. Same trick every single time. It’s the same boring trick every time. The user agent often shows curl, Python-urllib, or something clearly automated.
Count how many times the address appears in the last 24 hours. A handful of hits spread out over weeks almost always means harmless noise. Dozens or hundreds of requests in a short burst point to active scanning.
Check if other invalid addresses appear around the same time. When you see 64.277.120.231 mixed with 192.168.256.1, 10.300.0.1, or addresses containing letters, you can confidently label the whole group as bot garbage.
Practical Actions to Reduce Noise from Invalid IPs Like 64.277.120.231
Add a simple filter at the web server level. In Nginx, add one easy rule: if any part of the IP is bigger than 255, throw the request away before it touches your site. Apache users can do the same thing with a small mod_rewrite rule or a tiny Fail2Ban filter made just for bad IPs.
Also set a simple alarm: “If I see more than 20 fake IPs in 5 minutes, send me a message.” That way, you only get warned when something big is happening. This way, you ignore the occasional stray entry but still catch aggressive scanners.
Clean your analytics tools. Tools like Google Analytics and Matomo count every visit, even the junk from 64.277.120.231.
Just make a simple filter. Tell them: “Don’t count any visitor whose IP looks wrong.” After that, your numbers show only real people. Your reports become accurate overnight. SiteLike.org3
Is 64.277.120.231 Ever Dangerous?
By itself, no. A fake address like this can’t send viruses or attack you. The messages never get to a real computer, so nothing bad can happen. The presence of 64.277.120.231 serves only as a symptom. What matters is the behaviour around it. If the same bot also tries to hack your login or stuff bad code into your forms, block the whole attack right away. Don’t worry about the fake address; just stop everything that bot is doing.
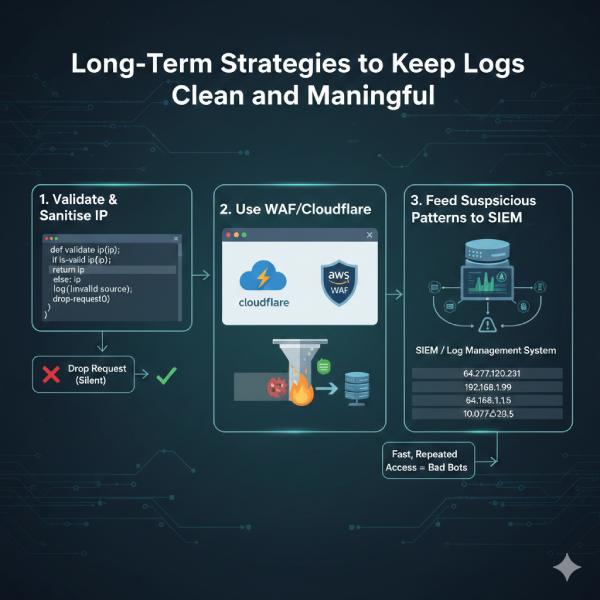
Long-Term Strategies to Keep Logs Clean and Meaningful
Validate and sanitise every IP address at the earliest possible point in your stack. A small function in Python, PHP, Go, or Node.js can catch octet errors before anything reaches the log file. Return a clear “invalid source” message and drop the request silently.
Use a tool like Cloudflare or AWS WAF. These tools sit in front of your site and throw away the bad or broken requests before they ever reach your server. They do the work for you automatically.
Feed suspicious patterns into your SIEM or log management system. 64.277.120.231 is not bad by itself. But if a bunch of these fake addresses show up fast, it usually means bad bots are sniffing around your site to plan an attack later.
FAQs
Is 64.277.120.231 a dangerous IP?
No, it is not dangerous at all. It is a fake address that no real computer can use. Nothing bad can come from it.
Why do I keep seeing 64.277.120.231 in my logs?
It shows up because lazy bots or broken programs write it by mistake. They don’t check if the address is real before sending it. That’s why it keeps popping up in your files.
Can this fake address send me viruses?
No, it can’t. Messages from a fake address never reach any real computer. It’s like sending a letter to a house that doesn’t exist; nothing happens.
Should I block 64.277.120.231?
Yes, you can safely block all fake-looking addresses. It stops junk and keeps your logs nice and clean. It only takes a minute to set up.
Is 64.227.120.231 the same thing?
No, that one is real and belongs to DigitalOcean in New York. Most of the time, it is safe and clean. It’s just a normal server.
What if I see tons of fake addresses all at once?
That means bad bots are looking around your site to find weak spots. Watch out, block them fast, and maybe turn on extra protection.
How do I stop this junk from filling my logs?
Use Cloudflare or add one easy rule in Nginx or Apache. These tools throw away the junk before it ever touches your server. Super simple and works great.
Do I need to report 64.277.120.231 anywhere?
No, you don’t need to report it. It’s only noise, not a real attacker. Save your time for real problems.
Will it mess up my Google Analytics numbers?
Yes, it will count as fake visits and make your numbers look wrong. Add one quick filter to skip bad IPs and only real people will show up.
Conclusion
The address 64.277.120.231 is just junk. It comes from bad bots, broken code, or tools that someone set up incorrectly.
This junk cannot hurt your server at all. It only makes your logs messy, messes up your reports, and makes you waste time looking at it.
When you know what it is, you can block it or hide it in just a few minutes. After that, your logs stay nice and clean.
Now you know exactly how to find and get rid of this kind of junk for good!
Have you seen 64.277.120.231 or other weird addresses in your logs lately? What steps did you take to clean them up? Let me know in the comments. I read every reply.
